Implementing access control – Secure Design Patterns for Multi-Tenancy in Shared Environments
Implementing access control
Once tenants are authenticated, the next crucial step is to enforce appropriate access controls based on their identities. Cognito identities can be integrated with IAM to create a seamless and secure access control framework. By associating Cognito identities with IAM roles, you can define what actions a tenant is allowed to perform and which resources they can access.
RBAC
RBAC is a widely used model for enforcing access controls in a multi-tenant environment. In AWS, you can create separate IAM roles for each tenant, each with its own set of permissions. This not only isolates each tenant but also makes it easier to manage and audit, as each role’s activities can be tracked independently.
Storing tenant-to-role mappings in an external database is a best practice that enhances security by keeping this sensitive mapping information out of IAM. Automation can be employed to handle the provisioning of new IAM roles and policies whenever a new tenant is onboarded, reducing administrative overhead. IAM role tagging can be used to further categorize and isolate roles, making it easier to manage roles across multiple tenants.
ABAC
ABAC offers a more flexible and granular approach to access control compared to RBAC. Instead of relying solely on roles, ABAC uses attributes—such as tenant ID or other tags—to dynamically enforce access policies. This makes ABAC particularly useful for multi-tenant architectures.
Shared IAM policies
One of the key advantages of using ABAC in a multi-tenant environment is the ability to create shared IAM policies that can be applied across multiple tenants. This is particularly beneficial for scalability, as there is no need to rewrite IAM permissions for every new tenant that comes on board. By using attributes, you can create a single IAM policy that dynamically adjusts its permissions based on the tenant making the request. This not only simplifies management but also ensures that the principle of least privilege is enforced, as permissions are granted based on specific attributes tied to end-user identities.
The following diagram (Figure 8.5) illustrates an example of ABAC implementation based on tags assigned to both users and resources. In this example, only users tagged with Tenant and assigned the value A can access resources tagged with the same value. This access control is facilitated through a single IAM policy shared among tenants. Within this policy, IAM conditions are utilized to match user tags with resource tags:
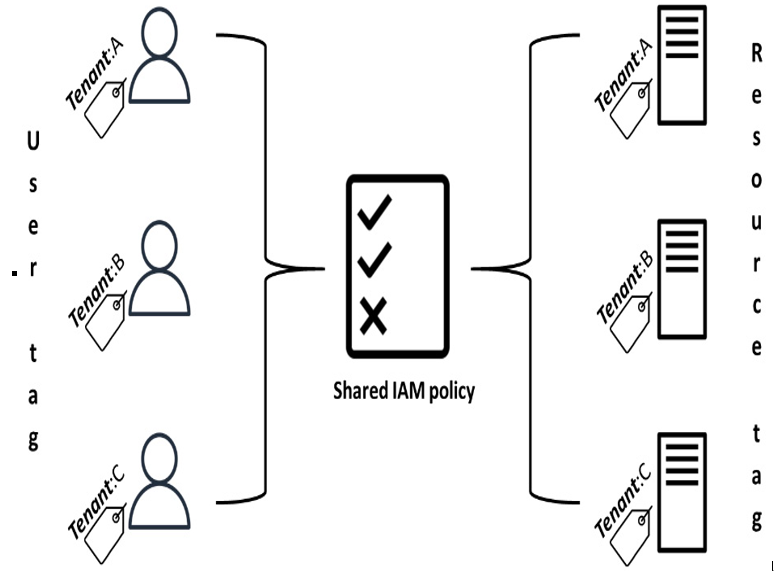
Figure 8.5 – ABAC example based on tags to isolate tenant access
