Advantages of ABAC with shared resources
ABAC is not only scalable and secure but also cost effective, especially when dealing with shared resources in a pool model. By using attributes to control access, you can securely share resources such as databases or storage buckets among multiple tenants. Each tenant’s access is restricted based on their specific attributes, ensuring that they can only interact with the portions of the shared resource that they are authorized to access.
Identity propagation
In a multi-tenant environment, the seamless transfer of tenant identities is crucial for maintaining robust access control and tenant isolation. One effective way to achieve this is by leveraging Cognito with JWTs to propagate tenant identifiers throughout the system. Specifically, the following steps can be followed as illustrated in Figure 8.6:
- The user first authenticates via Cognito.
- Cognito triggers a PreTokenGeneration Lambda function post-authentication. This function is invoked right after a user is authenticated and its purpose is to enrich the JWT token with additional claims, specifically those related to tenant identification.
- The PreTokenGeneration Lambda function parses the user’s attributes stored in Cognito to determine which tenant the user belongs to. The identified tenant ID is then added to the JWT as a custom claim, making it part of the token that will be used for subsequent interactions.
- After adding the necessary claims, the enriched JWT is signed and returned by Cognito to the user. It will serve as the user’s credential for subsequent interactions with the application.
- The authenticated user then sends a request to the API Gateway.
- Upon receiving the request, the API Gateway uses a Cognito user pools authorizer to validate the enriched JWT.
- Once validated, the API Gateway passes the enriched JWT to the application layer together with the request payload.
- Every component of the application receiving the payload from the request will also validate the enriched JWT token. This token can be verified by calling Cognito’s API to ensure its validity and the integrity of the tenant information it carries. The application then will authorize or decline the request depending on the verified tenant information.
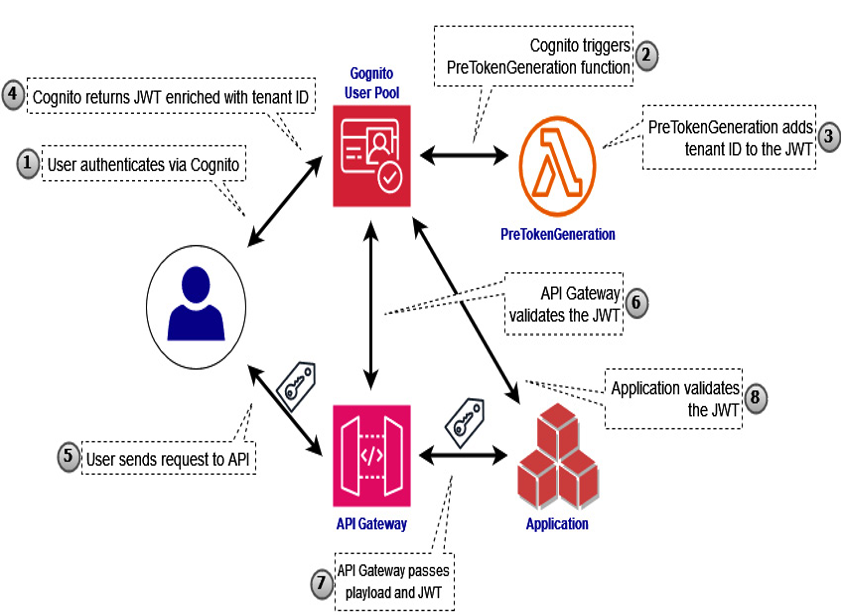
Figure 8.6 – Identity propagation process based on the JWT token
This approach to identity propagation is highly effective in ensuring that each tenant’s users can only access the resources and data they are authorized to. It also allows for tenant-aware authorization as the JWT, enriched with tenant-specific claims, navigates through requests between different services.
